Windows 7 Licensing a "Disaster" For XP Shops
PCs bought after April 22, 2010, however, can only be downgraded to Vista — no help for XP-based organizations, which would be wise to wait 12 to 18 months before adopting Windows 7, so that they can test hardware and software compatibility and ensure their vendors' Windows 7 support meets their needs. XP shops that chose not to install Vista will have to either rush their migration process or spend extra to enroll in Microsoft's Software Assurance program, which allows them to install any OS version — for about $90 per year per PC.
Microsoft to Release Record Setting Number of Critical Security Updates
'This is a very broad bunch,' said Wolfgang Kandek, CTO at Qualys, 'compared to last month, which was really all about PowerPoint. You've got to work everywhere, servers and workstations, and even Macs if you have them. It's not getting any better, the number of vulnerabilities [Microsoft discloses] continues to grow.'
Microsoft to Excel Users: Wiggle Your Mouse
We've all heard of crazy "workarounds" as they're called - this one takes the cake.
This is a workaround for a data import function into Microsoft Excel. What is Microsoft's grand solution if it locks up while you're attempting this? Wiggle your mouse.
Method 2: Move Your Mouse Pointer
If you move your mouse pointer continuously while the data is being returned to Microsoft Excel, the query may not fail. Do not stop moving the mouse until all the data has been returned to Microsoft Excel.
NOTE: Depending on your query, it may take several minutes to return the results of your query to the worksheet.
Read more at: http://support.microsoft.com/kb/168702
Password Stealer Found on New Netbooks
"Installed along with the worm was a rootkit and a password stealer that harvests log-in credentials for online ... To ensure that a new PC is malware-free, [Kaspersky] recommended that before users connect the machine to the Internet, they install security software, update it by retrieving the latest definition file on another computer, and transferring that update to the new system, then running a full antivirus scan."
Gartner tells businesses: forget about Vista
Companies have traditionally been advised to wait until the first Service Pack of an operating system arrives before considering migration.
However, Gartner is urging organisations that aren't already midway through Vista deployments to give the much-maligned operating system a miss.
"Skip Vista and target Windows 7," Gartner analysts Michael Silver and Stephen Kleynhans advise in a research paper. "Preparing for Vista will require the same amount of effort as preparing for Windows 7, so at this point, targeting Windows 7 would add less than six months to the schedule and would result in a plan that is more politically palatable, better for users, and results in greater longevity."
Even businesses that are midway through planning a Vista migration are urged to consider scrapping the deployment. "Consider switching to Windows 7 if it would delay deployment by six months or less," the pair advise. "The further you are withyour Vista plans, the more sense it makes to continue." Companies who are in the midst of a deployment should carry on, the Gartner team says, although they should plan to move again to Windows 7 in "late 2010 or early 2011". The Gartner experts say all companies should move off Windows XP by the end of 2012 to avoid problems with application compatibility. Read more at http://www.pcpro.co.uk/news/252955/gartner-tells-businesses-forget-about-vista.html#
ARS TECHNICA: 2009 Flash Drive Roundup
Consider the following factors:
- The majority of flash drives sold are either 4GB or 8GB, which is more than plenty of storage for most people.
- Most of the drives in this size range are under $20.
- Accessories (like neck straps, USB extension cables, spare caps, etc.) are no longer included.
Normally, twenty dollars is not something that most of us would think twice about, but don't most of us still want to know that we are getting our money's worth? To test this commodity theory, we selected a cornucopia of mostly 4GB and 8GB USB flash drives ranging from $9 to $30 dollars (average: $19.00)
Read more on Ars website (www.arstechnica.com) ..Microsoft's Life Cycle for Windows - The Death of 2000, and soon XP.
This is why NO ONE should be running Windows 2000 or Millennium (ME) anymore (or earlier, i.e. 98, NT, 95, etc). The last sentence sums it up very nicely. Even with a current anti-virus subscription, you are NOT protected!
"Recently, the Conficker/Downadup worm infected several hundred machines and critical medical equipment in an undisclosed number of US hospitals. The attacks were not widespread; however, Marcus Sachs, director of the SANS Internet Storm Center, told CNET News that it raises the awareness of what we would do if there were millions of computers infected in hospitals or in critical infrastructure locations. It's not clear how the devices (including heart monitors, MRI machines and PCs) got infected. Infected computers were running Windows NT and Windows 2000 in a local area network (LAN) that wasn't supposed to be Internet accessible, but the LAN was connected to one with direct Internet access. A patch was released by Microsoft last October by November that fixes the problem, but the computers infected were reportedly too old to be patched."
Researchers Find Massive Botnet On Nearly 2 Million Infected Consumer, Business, Government PCs
Researchers have discovered a major botnet operating out of the Ukraine that has infected 1.9 million machines, including large corporate and government PCs mainly in the U.S.
The botnet, which appears to be larger than the infamous Storm botnet was in its heyday, has infected machines from some 77 government-owned domains -- 51 of which are U.S. government ones, according to Ophir Shalltin, marketing director of Finjan, which recently found the botnet. Shalltin says the botnet is controlled by six individuals and is hosted in Ukraine.
Aside from its massive size and scope, what is also striking about the botnet is what its malware can do to an infected machine. The malware lets an attacker read the victim's email, communicate via HTTP in the botnet, inject code into other processes, visit Websites without the user knowing, and register as a background service on the infected machine, for instance. The bots communicate with their command and control systems via HTTP.
Botnet expert Joe Stewart says it appears to be similar to other downloader-type botnets. "It looks a lot like other downloader bots out there," says Stewart, director of malware research for SecureWorks. "It has a system for installing other malware and getting paid for it. The first stage is to get the bot piece onto the machine, and then they get paid to install other malware."
Finjan says victims are infected when visiting legitimate Websites containing a Trojan that the company says is detected by only four of 39 anti-malware tools, according to a VirusTotal report run by Finjan researchers.
"We don't have our hands on the actual [stolen] data, but we can tell a lot of what they [may be] doing with it by the malware," Shalltin says. "They can use it for spam, [stealing data], and almost almost anything."
Around 45 percent of the bots are in the U.S., and the machines are Windows XP. Nearly 80 percent run Internet Explorer; 15 percent, Firefox; 3 percent, Opera; and 1 percent Safari. Finjan says the bots were found in banks and large corporations, as well as consumer machines.
Shalltin says it appears that the botnet operators may be buying and selling bots or portions of their botnet based on a communique Finjan discovered on an underground black-hat hacker forum in Russia.
Conficker Launches April 1 (and no this isn't a joke)
The scariest thing about the Conficker worm is that literally millions of infected Windows PCs could be linked together to do its bidding. The second scariest thing is that no one really knows what its creator is going to do with this virtual army on April 1, when it's scheduled to contact a server for instructions. It's so bad, Microsoft has a running $250,000 bounty for the author, dead or alive. (Well, they probably want him alive, but they hate his guts.)
The New York Times' John Markoff rounded up some of the more ingeniously evil possibilities in a compelling article, the most sinister being a "Dark Google," postulated by University of California at San Diego researcher Stefan Savage, that would let bad people scour zombie machines all around the world for data to sell to other bad people.
But let's back up a bit. Conficker—whose weird name is a combination of "configuration" and a slightly more polite word for f***er, according to Urban Dictionary—actually began life as a lowly, "not very successful" worm in November, says Vincent Weafer, VP at Symantec Security Response. Weafer told us it exploited a Microsoft remote server vulnerability that had already been announced and patched the previous month, so the only systems that were vulnerable were the ones that weren't up to date.
The B release, pushed in December, on the other hand, was "wildly successful," says Weafer, infecting millions of unpatched computers because it's an aggressive little bastard—the first worm in years on a scale like Blaster. It has built-in p2p capabilities, and brute forces its way into open shared folders or printers, so it can crawl an office network quickly. It also piggybacks onto USB flash and hard drives. On top of all that, it's designed to be incredibly resilient, killing security software, disabling Windows Update, and digging down deep.
The C release came out this past month. It doesn't go after new machines—it's actually a payload for computers already infected with B. It transformed Conficker from a sneezing pandemic into a seriously nasty plague. With C, its p2p powers are extended further, with digital code-signing, so it only accepts trusted code updates from itself. That means security experts can't simply inject code to neutralize it. The patch also made Conficker better at killing security software. And it expanded the scope of the domains it tries to contact for instructions from 250 to 50,000, completely neutralizing security experts' previous tactic of seizing the domains. There's effectively no way to the cut the head off of this demon snake. The stage is set: On April 1, Conficker will reach out for the millions-strong zombienet's next set of instructions.
So what will happen? Well, no one knows for sure. Conficker's creator can do whatever he wants with his army. Launch massive denial-of-service attacks, setup the "Dark Google" syndicate, target millions of new machines, or generate a tidal wave of spam that'll crash against servers all over the world.
Most likely though, Weafer told us, Conficker's creator is motivated by money—they'll rent it out. And if Conficker's used as a massive doomsday tool, they'll "quickly lose the ability to make money" with it. A low key operation harnessing the power of computers that are mainly located in developing nations may not have a big impact, though it would certainly set a terrible precedent: Whatever Conficker's results, they will lead others to develop this idea in frightening new directions.
Conficker's innovative approach that utilizes p2p, code-signing and a distributed domain setup will very possibly serve as inspiration to other malware writers, who Weafer said "you can bet" are watching Conficker's success very closely, just as Conficker's creators have clearly learned from past malware. It's like evil open source.
That doesn't mean April 1 will be a "digital Pearl Harbor." If your machine is patched and up to date, the Microsoft Report's Ed Bott tells us, you'll probably be totally fine. And yes, you can get rid of it if you happen to be infected. There is an outside chance Conficker could turn into a massive parallel computer that borders on self-aware, come April 1, but more than likely, the day will come and go without you noticing anything weird, just some extra spam in your box for some V@ltr3xxx.Conficker Worm Gets an Evil Twin
The criminals behind the widespread Conficker worm have released a new version of the malware that could signal a major shift in the way the worm operates.
The new variant, dubbed Conficker B++, was spotted three days ago by SRI International researchers, who published details of the new code on Thursday. To the untrained eye, the new variant looks almost identical to the previous version of the worm, Conficker B. But the B++ variant uses new techniques to download software, giving its creators more flexibility in what they can do with infected machines.
Conficker-infected machines could be used for nasty stuff -- sending spam, logging keystrokes, or launching denial of service (DoS) attacks, but an ad hoc group calling itself the Conficker Cabal has largely prevented this from happening. They've kept Conficker under control by cracking the algorithm the software uses to find one of thousands of rendezvous points on the Internet where it can look for new code. These rendezvous points use unique domain names, such as pwulrrog.org, that the Conficker Cabal has worked hard to register and keep out of the hands of the criminals.
The new B++ variant uses the same algorithm to look for rendezvous points, but it also gives the creators two new techniques that skip them altogether. That means that the Cabal's most successful technique could be bypassed.
Conficker underwent a major rewrite in December, when the B variant was released. But this latest B++ version includes more subtle changes, according to Phil Porras, a program director with SRI. "This is a more surgical set of changes that they've made," he said.
To put things in perspective: There were 297 subroutines in Conficker B; 39 new routines were added in B++ and three existing subroutines were modified, SRI wrote in a report on the new variant. B++ suggests "the malware authors may be seeking new ways to obviate the need for Internet rendezvous points altogether," the report states.
Porras could not say how long Conficker B++ has been in circulation, but it first appeared on Feb. 6, according to a researcher using the pseudonym Jart Armin, who works on the Hostexploit.com Web site, which has tracked Conficker.
Though he does not know whether B++ was created in response to the Cabal's work, "it does make the botnet more robust and it does mitigate some of the Cabal's work," Support Intelligence CEO Rick Wesson said in an e-mail interview.
Also known as Downadup, Conficker spreads using a variety of techniques. It exploits a dangerous Windows bug to attack computers on a local area network, and it can also spread via USB devices such as cameras or storage devices. All variants of Conficker have now infected about 10.5 million computers, according to SRI.
Microsoft Slaps $250K Bounty On Conficker Worm
The Microsoft Windows 7 Upgrade Program
"Conficker" Infects 9 Million Over the Weekend
Initially it was reported Conficker, or Downadup, focused on machines that weren't patched with a Microsoft emergency fix released last October (MS008-067).
However since then, the bug has evolved and is now able to spread to patched computers through portable USB drives.
Once in the machine, the worm can browse through the network the computer is connected to and copy itself to other machines, according to the article. This means users do not have to be at their computers or even logged on for the bug to spread.
Infected machines can potentially reveal users' personal and financial information, though it is unclear if that is the objective of the cybercriminals behind the attack. With the presidential inauguration scheduled for today, it's possible the cybercriminals may act then, since they traditionally like to coincide attacks with large events.
The Internet GateKeepers at Google
Which Web Browser is King?
It's a highly debatable topic, one that tends to be subjective and fraught with inconsistencies. For example, latency on the Internet can dramatically affect browser speed. One day, Google Chrome can load IGN.com faster than butter on a banana, the next day (say, when a new Gears of War 2 review posts), latency can slow the site to a crawl, and Chrome seems like a dud. That's why, when you see speed tests for browser that claim "Chrome loads faster" it's important to ask a few questions: loaded when, over what broadband speed, with what other apps running, on what machine?
Speed, of course, isn't everything. We ran into an interesting compatibility glitch or two completing some of our tests. If a browser can't finish a particular benchmark, it doesn't get a score.
What does it mean, ultimately? For the average user, it may not mean much. But for those of us who spend vast amounts of time on the Internet, for work and play, browser performance is a big issue. Waiting for sites to load is no fun when you're trying to get work done.
Let's dive into the testing methodology. Continued...
Microsoft Takes 7 Years to Release Security Patch
Windows 7 Benchmarks Show Little Improvement On Vista
"In fact, as I worked my way through the process lists of the two operating systems, I was struck by the extent of the similarities," Kennedy writes, before discussing the results of a nine-way workload test scenario he performed on Windows 7 — the same scenario that showed Vista was 40 percent slower than Windows XP.
"In a nutshell, Windows 7 M3 is a virtual twin of Vista when it comes to performance," Kennedy concludes. "In other words, Microsoft's follow-up to its most unpopular OS release since Windows Me threatens to deliver zero measurable performance benefits while introducing new and potentially crippling compatibility issues."
Recession Proof: Improving Your ROI during down periods
While consumer spending has slowed down since the financial meltdown last year, these trends provide an opportunity, as well as a challenge, for small businesses today. Since you're reading this newsletter, you're already savvy enough to appreciate the value of smart web marketing - online marketing channels allow you to target your audience with special offers, unique up-sells and value-add propositions that can help increase your revenue even while overall consumer spending is down.

In today's economy, there are no "one size fits all" offers - each consumer responds to a different message, price point and feature set before deciding on a purchase. Given the ease of comparison shopping, there are dozens of vendors within each industry vying for new business. Since you can segment your search ads, landing pages and product offerings for each type of consumer, it's possible to out flank your competition through improved targeting.
Suppose you're a dentist serving a college town and looking to expand new clients. Rather than just providing standard ads with your contact information you can offer specials such as free teeth whitening when you refer a friend or 50% off initial visits for new students. These types of offers resonate with the demographic you are targeting, and, when combined with the proper graphics, can result in higher conversion rates.
Intelligent web marketing
can help you generate new business during a recession, since consumers are
always looking to save or upgrade their vendors. By providing a cost-effective,
intelligent set of features for your consumers, you can grow your bottom line even as the economy is shrinking.
Fake popup study sadly confirms most users are idiots
The authors, who work in the Psychology Department of North Carolina State University, crafted a set of four fake dialog boxes. All of them contained the following warning: "The instruction at '0x77f41d24 referenced memory at '0x595c2a4c.' The memory could not be 'read.' Click OK to terminate program." One of the warnings was indistinguishable from the standard Windows XP system dialog, but the remaining three were had a number of warning signs that should tip off users to potential malware.
In all cases, mousing over the "OK" button would cause the cursor to turn into a hand button, behavior more typical of a browser control; all dialogs also had minimize and maximize buttons, while a second added a browser status bar to the bottom of the window. Finally, the most blatant one alternated between black text and a white background and a white-on-black theme. All of these should metaphorically scream, "This is not safe!"
The researchers then created a Flash application that would mimic loading a series of medical websites. They told a panel of 42 college students that they were supposed to watch as the sites loaded and then would be asked a series of questions about the sites. Instead, the fake dialogs were loaded in a random order and the users' responses were tracked.
Of the 42 students, 26 clicked the OK button for the "real" dialog. But 25 clicked the same button for two of the fakes, and 23 hit OK on the third (the one with the status bar showing). Only nine of them closed the window—two fewer than had closed the real dialog. In all cases, a few of the users simply minimized the window or dragged it out of the way, presumably leaving the machine's next user at risk.
 The response time, which tracked how long it took the users to perform any action, was not significantly different among the different dialogs, indicating that there wasn't even any thought expended on evaluating the fakes.
The response time, which tracked how long it took the users to perform any action, was not significantly different among the different dialogs, indicating that there wasn't even any thought expended on evaluating the fakes.
Follow-up questions revealed that the students seemed to find any dialog box a distraction from their assigned task; nearly half said that all they cared about was getting rid of these dialogs. The results suggest that a familiarity with Windows dialogs have bred a degree of contempt and that users simply don't care what the boxes say anymore.
The authors suggest that user training might help more people recognize the risks involved with fake popups and the diagnostic signs of genuine Windows dialogs, but the fact that the students didn't appear to spend any more time evaluating the fake dialogs raises questions as to whether education is enough.
The study will appear in the Proceedings of the Human Factors and Ergonomics Society.
SmartBox Recommended Software
If you've been thinking about renewing your anti-virus subscription and getting up to date, or maybe about upgrading your computer with the latest version of PowerDVD, we've got great deals on them all.
If you have multiple computers that need protection, or want to get more than one year of protection at a time, take a look at our package deals. I don't think you can find a better price anywhere.
Best yet, when you buy your software through us, we'll offer you 50% Off an On-Site Service Call. Call Us Now for more details!
Meantime, checkout our pricing at http://software.smartboxllc.com.
All the Best,
Colin Receveur
colin@smartboxllc.com
(502) 741-1413
www.SmartBoxllc.com
Computer Repair 101 - Just Hold the Repairman Hostage
According to Halifax Police, Ms. Sinclair was enraged with Mr. Scott. "She told the technician, in a tirade, that he was not leaving until her Internet was working and she told him she was keeping him hostage," Constable Jeff Carr said.
"She implied that she had a gun, although he didn't see one."
The repairman told Ms. Sinclair he could fix her computer, but first had to retrieve a disc from his truck, according to the police version of events. Ms. Sinclair followed Mr. Scott downstairs, but he was able to run away and drive to the Aliant office.
Mrs. Sinclair denies the allegations and says that she merely stated, 'I don't want to hold you hostage, but would you mind hanging around until the other technician arrives so that the two of you can sort it out.' She was arraigned in Halifax Provincial Court Friday and is now free on conditions including that she have no contact with the repairman or any employee from her ISP.
Google Releases Own Browser - Chrome
Google Picasa 3.0 - Now With Facial Recognition
A Good Reason To Go Full-Time SSL For Gmail
Last week Google introduced a new feature in Gmail that allows users to permanently switch on SSL and use it for every action involving Gmail, and not only, authentication. Users who did not turn it on now have a serious reason to do so as Mike Perry, the reverse engineer from San Francisco who developed the tool is planning to release it in two weeks.
When you log in to Gmail the website sends a cookie (a text file) containing your session ID to the browser. This file makes it possible for the website to know that you are authenticated and keep you logged in for two weeks, unless you manually hit the sign out button. When you hit sign out this cookie is cleared.
Read more @ Hungry Hackers
Intel Releases USB 3.0 Specs
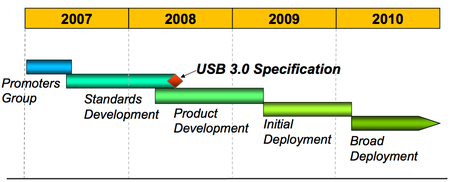
USB 3.0 is set to deliver data-transfer speeds of up to 5Gb/s, initially over tweaked connectors and wiring and, later, over optical links.
XP Still Killing Vista in Sales
Microsoft Distorts Vista Sales Figures
While Microsoft excitedly tries to sway public opinion by touting that Windows Vista License sales top 180 Million units, Hewlett-Packard (HP) was busy smacking Microsoft down -- reportedly shipping PCs with a Vista Business license but with Windows XP pre-loaded in the majority of business computers sold since the June 30 Windows XP execution date established by Microsoft -- casting a lot of doubt over how many copies of Vista have actually been sold.
In other words, Microsoft counts a sale for Windows Vista even though the computer manufacturer actually sold Windows XP. It's kind of ironic when you realize how desperate Microsoft has become to gain public acceptance for the dying operating system. Dell and other computer manufacturers are reportedly also shipping computers 'downgraded' to Windows XP.
Microsoft has told HP they won't be able to do that after January 2009, but HP is already discussing how to push that deadline back with Microsoft. Feedback from HP customers reveals that they hadn't had the time to do full compatibility testing of all their business applications with Vista and the high time and monetary costs of rebuilding system images wasn't worth it, especially in this economy.
Blu-Ray Bites The Dust TooIn other news, consumers do not want Blu-ray, says a research firm. A consumer survey done by ABI Research revealed that over half of the 1000 respondents had 'other priorities,' to buying a Blu-ray player, saying that they had no plans to purchase one; a further 23% are likely to buy, but not until sometime in 2009.
ABI Research principal analyst Steve Wilson said that there wasn't much value proposition seen in a Blu-ray player or in content "Consumers were happy to embrace standard DVD when that format arrived because the improvement in quality over VHS videotapes was dramatic. Standard DVD didn't require the purchase of a new TV either.
In contrast, while half of the respondents to our survey rated Blu-ray's quality as 'much better' than standard DVD, another 40% termed it only 'somewhat better,' and most are very satisfied with the performance of their current DVD players." Another reason cited was that a Blu-ray investment also dictates an HDTV purchase, something consumers are reluctant to do.
Why Power Failures Always Lead To Data Loss
But, what happens to your precious data when there is a power outage?
Will your file system recover? Properly? Are you sure?
Will you have to resort to your backup, just to be safe?
Maybe you need a UPS. Then again, maybe not. Either way, reading this article will help you to make that decision.
Colin Receveur
SmartBox, LLC
Survival Time of an Un-Patched Windows Computer?
As many of my current clients know, I've pushed routers (in conjunction with other security measures) upon all of them for security reasons. A few have called me paranoid, so it's nice to see a study backing up my paranoia! While they were more expensive several years ago, routers have come down to a point where even the simplest of home users can afford to have one protecting their computer system.
Concludes the ISC's Hutchinson: "While the survival time varies quite a bit across methods used, pretty much all agree that placing an unpatched Windows computer directly onto the Internet in the hope that it downloads the patches faster than it gets exploited are odds that you wouldn't bet on in Vegas."
Tweaking Your Windows Startup Routine
You probably have asked yourself before "What is all this crap that starts up when I turn my computer on?!"
You're not alone. 3rd party vendors load all kinds of junk software onto your computer. These programs all serve legitimate purposes, and are not intended to bog down your system, but they do. AIM, Antivirus programs, all of the little programs sitting in your task bar, and some programs you can’t see all contribute to the performance of your system.
Disabling unused Windows Startup Applications
The following steps will teach you how to remove programs and services from the startup sequence. Doing this will free up RAM memory, since those programs will not be running any more. It will also dramatically increase the time that your computer takes to turn on. To use this feature make sure you are logged in as an administrator.
- Click Start, then Run, and type msconfig in and press OK. A small System Configuration Utility dialog box will appear with many options like General, System.ini Win.ini, Boot.ini, Services, Startup and Tools. For now, we're going to ignore all of them except the Startup tab.
- Click on the Startup tab and uncheck the applications that you want to disable from your Windows startup sequence.
- Now click on Apply button to implement the changes, and restart your computer to put the changes into effect.
Go through the list and look for any familiar programs and disable those first, then go back and look at the unfamiliar programs and try to find out what application they belong to, Google the process name like ctfmon.exe and it should come up with a detailed use for the program in the listings and if it’s harmful or just a system program.
Voila! When your computer restarts, you will receive a notice that there were changes made to your startup sequence. This is normal. Check the "Do not show me this again" box and click OK!
Could You Imagine Still Being on Dial-Up Internet?
When asked what it would take to tempt them to switch, 35% said the price of broadband would have to fall, while almost a fifth said that nothing would tempt them to upgrade, suggesting many die-hard dial-up users simply don't see the need for the higher speeds that are available.
About 3.5% of the visitors to our website are still on dial-up as well.
You can read more of this article over on PCPro










